Credentials Are Tough By Design
Credentials in Cloudbees SDA are admittedly a little tricky to get to. This is by design. If it were any easier, it could be a potential security risk. There is really just one way to use credentials in code, and it’s a multi-step process. Here are the steps:
- Set the credential.
- Attach it to a step.
- Use it.
Careful manipulation is required here, as the software requires very exact definitions to get to this information. Any single missed parameter or missing ACL will return an error code.
How To Set The Credential
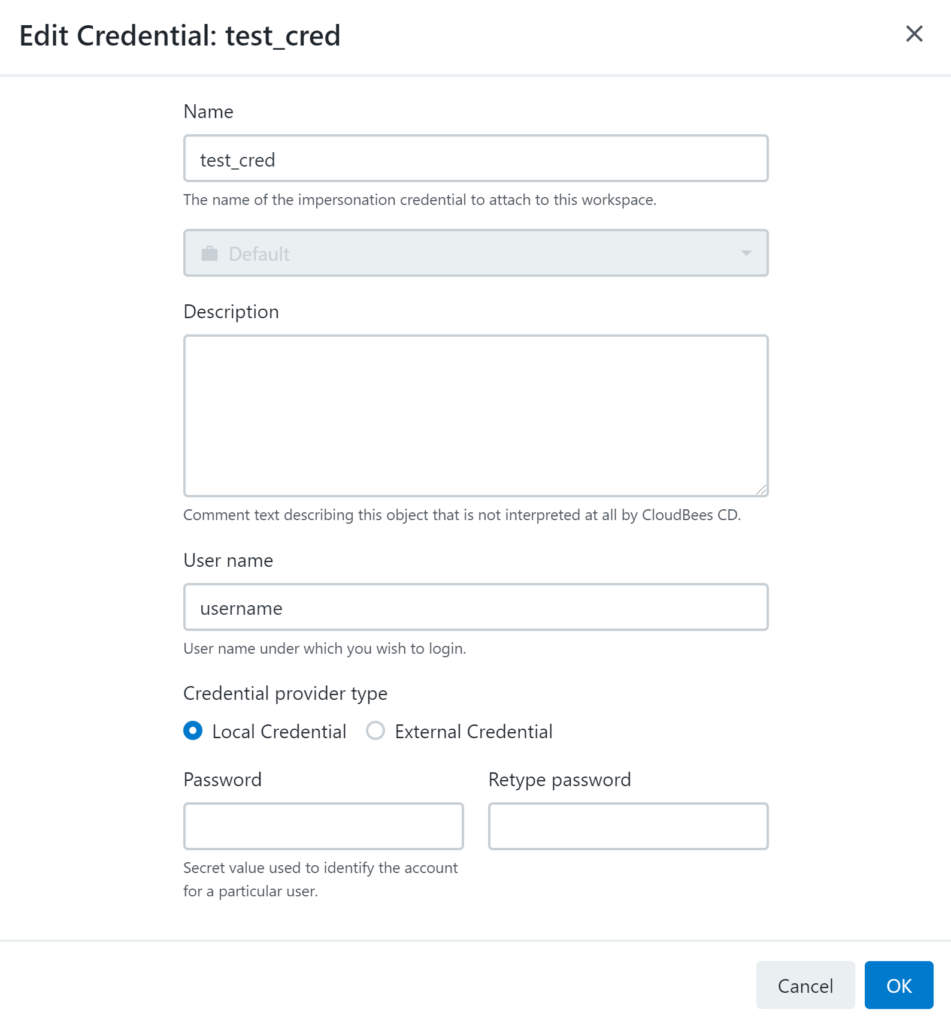
It is very simple to set a credential in CloudBees SDA. First, start at the project level, or go to the credential screen, and add a new cred. You’ll be able to add a name, description, username, password, and set it to a local or external credential. Once it’s set, hit OK and head to the location where you intend to use it.
Attachment
Once a credential is set, it’s available in any pipeline or procedure that can access that project. However, you will need to grant explicit access permission for the pipeline or procedure that will use it. You do this through the attaching feature. From within a pipeline, the code for this command looks like this:
ectool attachCredential "<project name>" "<credential name>" --pipelineName $[/myPipeline] --stageName $[/myStage] --taskName $[/myTask]
In this case, all of these flags are important. Please note that if you call it from a procedure context, you’ll need to use –stepName instead of –taskName, as these are different from pipeline tasks.
Using The Credential
Once the credential is attached to a task or step, using it is a simple matter. Use these two lines of code to pull the username or password into any script or bash command:
ectool getFullCredential "/projects/<project name>/credentials/<credential name>" --value password ectool getFullCredential "/projects/<project name>/credentials/<credential name>" --value userName
They can be set to variables or used inline, depending on the context, such as an API call to a third party tool. Credentials are a powerful tool in CloudBees SDA — they can be used for more than just basic authentication. You can save any kind of secret in the password field, including tokens, making them a convenient way to hide secure information with confidence.
If you have any questions about credentials in SDA, or need help getting started, reach out to us and we’d be happy to help.







