In a previous blog article I discussed, at a high level, the Integrity to Windchill integration for PTC Integrity Lifecycle Manager. Now that we have seen some of the context of how the Integration is supposed to work, I thought it would be a good idea to actually...
PDM/PLM-Product Data and Lifecycle Management
Podcast: Peter Thorne Discusses Hot Trends in Product Lifecycle Engineering Tools
SPK and Associates co-founder Chris McHale speaks with Peter Thorne, director at Cambashi, a Cambridge, England-based independent industry analyst firm. With his over 30 years of experience as a software engineer user, vendor, and now analyst, Peter's in a great...
Podcast: Oleg Shilovitsky Discusses the Difficulty BOM’s Across the Product Life Cycle
Last month, SPK and Associates co-founder Chris McHale spoke with PLM expert Oleg Shilovitsky on the difficulty of BOMs across engineering disciplines. In part two of the discussion, they focus in on the difficulty of BOMs across the product life cycle. This is...
Enhancing Electric Commander Build Processes by Creating Dynamic Job Steps
In a simple, straight-forward implementation of a continuous integration pipeline you would typically create a chain of procedures that perform the same set of operations on the supplied input. This provides a build process that is well-defined, repeatable,...
New Podcast: Talking Beyond PLM with PLM Expert Oleg Shilovitsky
SPK and Associates co-founder Chris McHale previously spoke with PLM expert Oleg Shilovitsky, founder of BeyondPLM.com, to get his top three product lifecycle management (PLM) predictions for 2015. Now they are teaming up monthly to discuss relevant industry items...
Electric Commander: Performance Comparison Between ectool and ec-perl
Prior to version 5.2, Electric Commander has offered two primary ways to access the API for scripting purposes: ectool and ec-perl. Both allow users to accomplish virtually any task within Commander, but it’s important to note there is a significant performance...
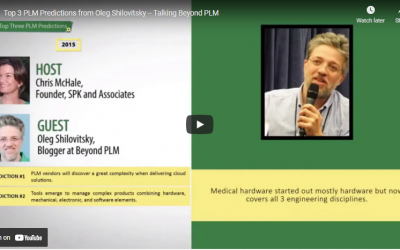
Top 3 PLM Predictions for 2015
SPK and Associates co-founder Chris McHale recently spoke with PLM expert Oleg Shilovitsky, founder of BeyondPLM.com, to get his top three product lifecycle management (PLM) predictions for 2015. 1. PLM vendors will encounter greater complexity when delivering cloud...
Bringing Your Own Apple Device and Developing a BYOD Policy
In today’s world, everyone has a mobile device; cell phones, tablets, or a hybrid of the two. In a blog post published on ZDNet in June 2014, Dimensional Research conducted a survey of more than 300 IT leaders, and concluded specifically Apple’s enterprise presence is...
Continuous Integration Best Practice: Including a Version Number in Builds
Building software source code is an integral part of continuous integration and is the backbone of developing useful software. By “build”, I mean that the source code needs to be received as input to a compiler and a binary of some sort emitted for the software to...
Bringing Your Own Android and Developing a BYOD Policy
The concept of letting employees bring their own phones and devices to work has become more and more common. Employees want to use their personal devices in the workplace without having to carry around a second device for personal use. While this helps with cost...
Medical Device Development: First to Market
In the world of fast competitive marketing, a lot of attention goes to the first company who develops a creative breakthrough and comes out with a cool new device first. New technology in the medical device market has resulted in several new products which include;...
MKSSI Environment Variable – an Integrity PLM Software Primer
I'm not a programmer by trade, so I've had to force feed myself a lot of knowledge – some of it makes sense, some of it is beyond me. I've written this post to serve as an Integrity PLM Software Primer for the MKSSI Environment Variable. I hope you find it useful!...