Recently, I was working on a custom API program for a customer, when I came across something that could be a sticky little problem for someone trying to add custom API programs to their PTC Integrity Lifecycle Manager Environment. The problem was first manifested when I had a Java based API application that I was trying to execute on my local desktop. This application was supposed to connect to the PTC Integrity Lifecycle Manager server to perform a series of operations. The problem was, I could never get a connection. Each time I would get a console error message that stated:
“error message = Failed to establish a session: Session not authenticated/authorized.”
Of course seeing this error message had me looking at the login credentials I was using for my API application. Of course I verified the credentials by logging in via the various clients. I even tried using alternate credentials, again with no success.
 The light didn’t actually turn on for me until I went and examined the Server.log file on my local PTC Integrity Lifecycle Manager server. In the server.log file I saw the following error message that corresponded with my attempts to connect to the PTC Integrity Lifecycle Manager server:
The light didn’t actually turn on for me until I went and examined the Server.log file on my local PTC Integrity Lifecycle Manager server. In the server.log file I saw the following error message that corresponded with my attempts to connect to the PTC Integrity Lifecycle Manager server:
***** ERROR ***** (0): ICAllowSpecificConnectionPolicy failed the connection. Connection: 10.29.98.135: is not on the list of acceptable machines.
Often when PTC Integrity Lifecycle Manager Servers are initially installed, certain environmental settings are made by default. The Connection Policies are one example of this. They are made in the <installation directory>/config/client/IntegrityClient.rc file on the server. The server, by default, was set up as follows:
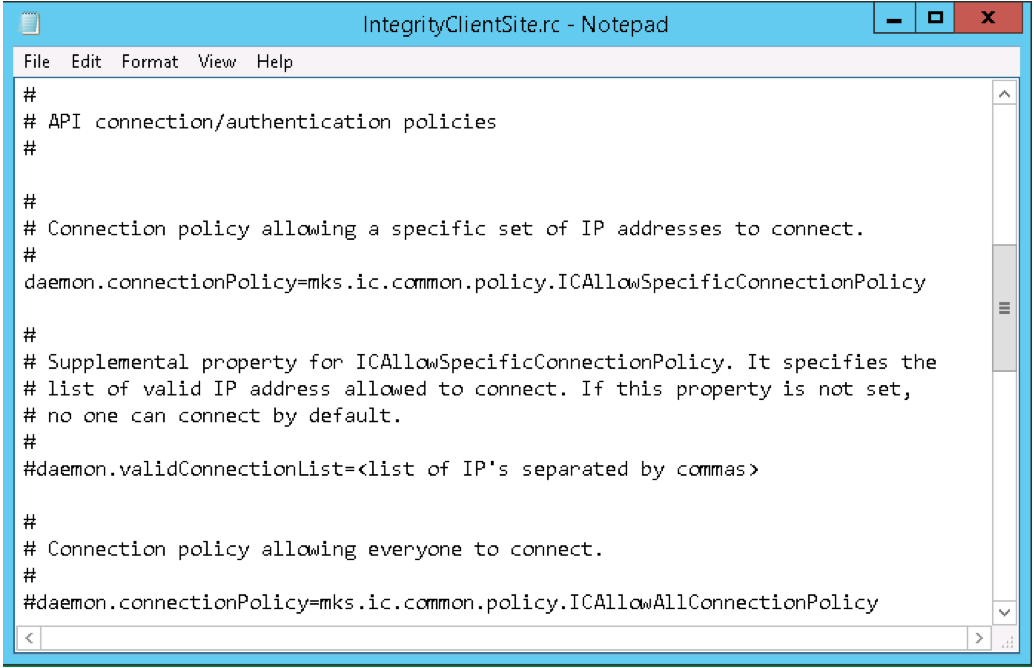
As you can see, through the ICAllowSpecificConnectionPolicy, the server was set-up to only allow API applications from a specific set of machines to connect to this server. That list of machines is controlled through the validConnectionList property. Since the list was never set up, no connections were allowed other than official PTC Integrity Lifecycle Manager Clients.
In truth, this functionality can be a powerful method of enforcing security across your organization. Maybe you only want your user community to connect using the official clients or maybe the only integrations you want running in your environment are those you write and deploy yourself. You can exert a level of control by only allowing API applications running on specific machines to connect to your server.
In my case though, the API application I was working with was one intended to be deployed to almost all the end-users. Maintaining that level of security was neither intended nor required. Therefore, I opted to go with the ICAllowAllConnectionPolicy as shown below:
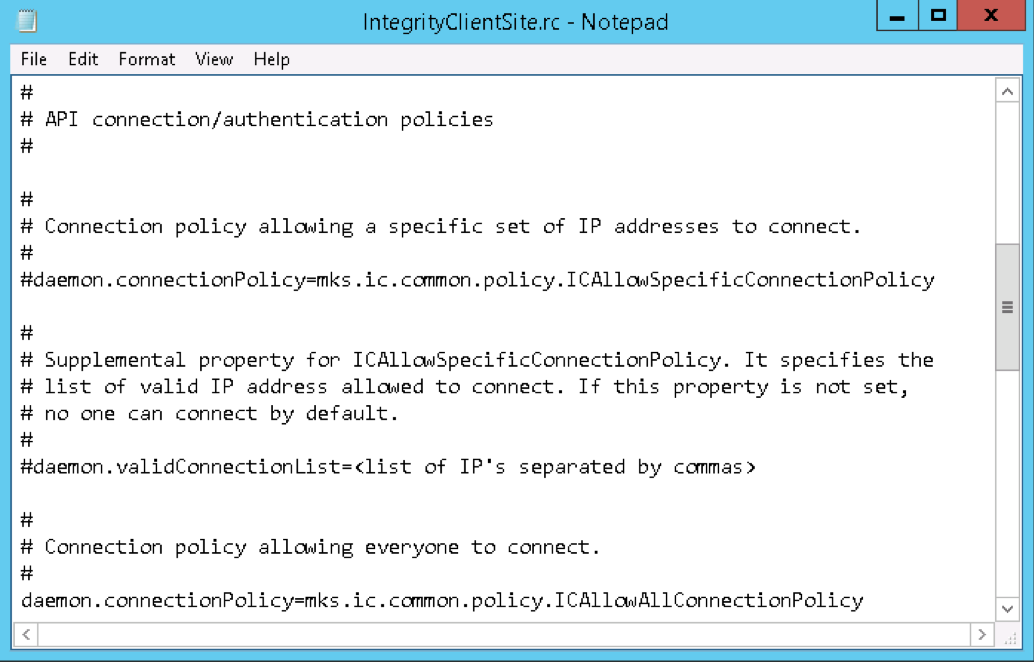
As you can see, I simply commented out the line for ICAllowSpecificConnectionPolicy, and un-commented the line for ICAllowAllConnectionPolicy. This allows all API applications to connect in the same manner as the official PTC Integrity Lifecycle Manager.
Once these changes were in place, and I cycled the PTC Integrity Lifecycle Manager server with the standard “mksis restart” command, my API application was able to connect to my PTC Integrity Lifecycle Manager server without issue.
Although the Connection Policies in PTC Integrity Lifecycle Manager initially started out as a sticky little problem with my API application, these policies can actually be quite a handy feature for those of you out there who want to maintain control over custom API applications being written against your PTC Integrity Lifecycle Manager Server.






