Recently I was doing some work for a customer, experimenting with allowing limited access to non-Administrator class users using the PTC Integrity Administration client. I discovered that once a standard user gained access to the PTC Integrity Administration client, there were plenty things they could potentially do that would cause an administrator all kinds of grief.
My task then was to lock down the PTC Integrity Administrator client so that if a standard user did somehow gain access to it, they wouldn’t be able to do anything to inadvertently damage the environment. The problem is that when you first install and configure the PTC Integrity server, many of the main ACLs (Access Control Lists) are set by default to allow “everyone” to have access to given portions of your server.
What I have provided below is a set of step by step instructions that can be followed to successfully lock down your PTC Integrity server by modifying a set of given ACLs. Each of these ACLs is accessed through the PTC Integrity Administration client.
1. Using the PTC Integrity Administration client, login as Administrator to the PTC Integrity server you wish to lock down.
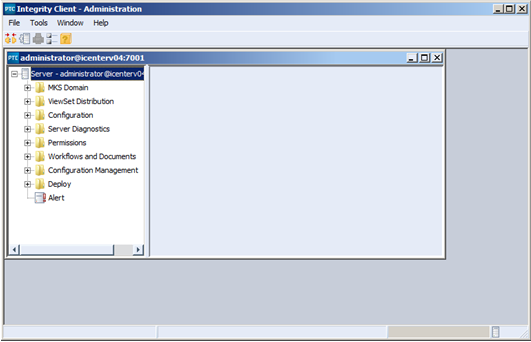
2. Expand the permissions block, select “All” and right click on MKS and select “View ACL”
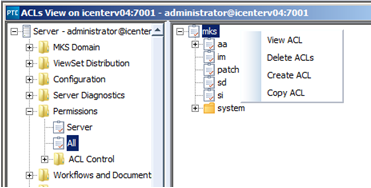
Note: Make sure you add the new principal to the system before you remove the permissions from the “everyone” group. Failure to do this may accidentally remove your ability to administer the server altogether.
3. This will open the ACL to edit. From this window you can remove all the permissions from the “everyone” group (except login permissions) and add a new principal (i.e. an Administrator user or domain group) with permissions to administer the server.
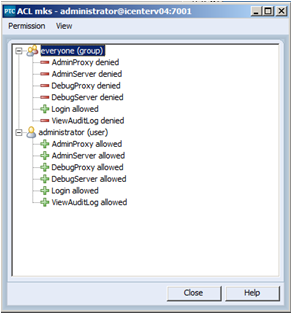
Note: Make sure you add the new principal to the system before you remove the permissions from the “everyone” group. Failure to do this may accidentally remove your ability to administer the server altogether.
4. Similarly the ACL for Permissions -> All -> IM should be reset as follows:
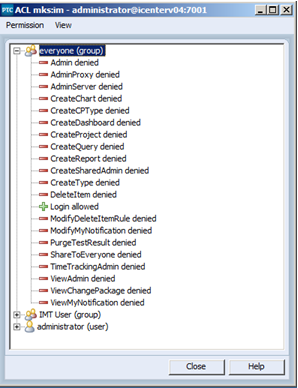
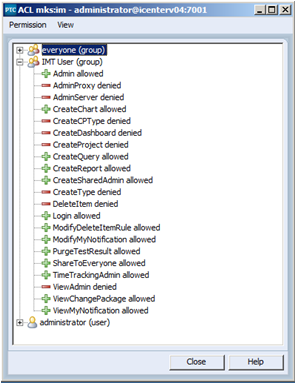
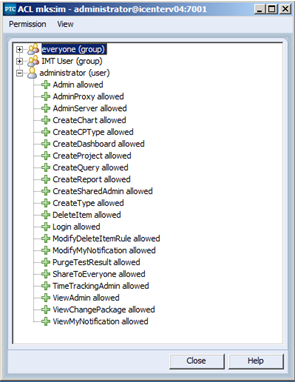
Note: In place of using the “everyone” group, I’ve created a generic MKS Domain group to which every user in the system will be a member upon registration.
5. Similarly the ACL for Permissions -> All -> SI should be reset as follows:
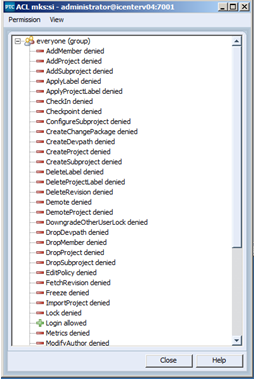
Note: In this example I have chosen to forgo adding extra principals for SI. On this particular server SI is not in use.
6. The next ACL to be updated is ACL Control. As you can see below two new principals (“Administrator” and the generic user group) are first added to the ACL and granted read and update permissions. Once that is complete, read and update permissions can then be taken away from the “everyone” group.
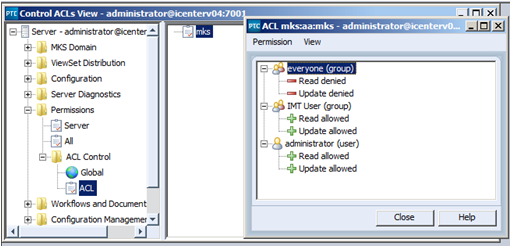
Note: It is extremely important that this ACL is updated as described above. Removing read and update permissions from “everyone” before you grant access to any other principal could result in you locking yourself out of your PTC Integrity server.
Conclusion
That’s pretty much all there is to it. Implementing this procedure on your local PTC Integrity server will ensure that only those users or groups to whom you grant access to will have permission to make changes using the PTC Integrity Administration Client.
Please note that if a user or group is granted administrator access for any project or type they will be able to make changes to that project or type, including creating new fields or states. In a future blog article I will look more closely at project based administrator permissions on your PTC Integrity server.
Next Steps:
- Contact SPK and Associates to see how we can help your organization with our ALM, PLM, and Engineering Tools Support services.
- Read our White Papers & Case Studies for examples of how SPK leverages technology to advance engineering and business for our clients.







