Let’s face it – data breaches are on the rise, and it’s costing organizations big money. Malicious insiders contribute to a third of these breaches, making the situation even trickier. Furthermore, there’s also the challenge of managing a growing amount of data and the need for tools making collaboration safe and secure. That’s why, as a certified Microsoft partner, we’re sharing how Microsoft Purview can fortify your data security in a straightforward and effective way.
Strengthening Security with Purview
Any CISO knows the importance of keeping data safe both now and for the long-term. Yet, reports show a whopping 83% of organizations face multiple data breaches, costing around $15.4 million on average.
Microsoft Purview is one of the strongest lines of defense to improve your data security. Check out how to use the best features of Purview
- Information Protection: It helps you find and categorize your data using smart tech. Your data gets protected with automated data discovery and classification.

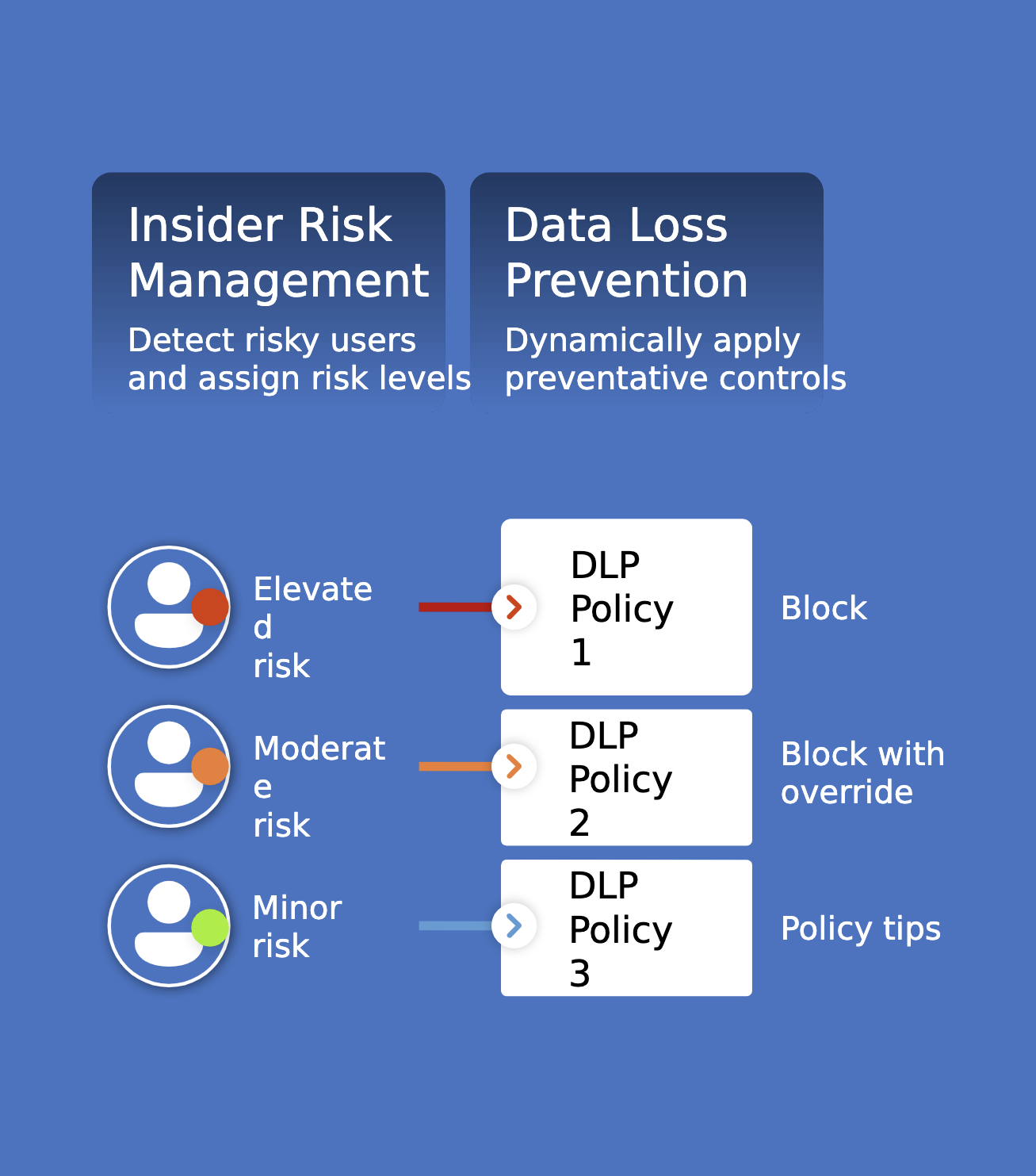
- Guard Against Insider Risks: This tool helps build a solid plan to tackle risks from inside your organization utilizing pseudonymization, strong privacy controls, and machine learning models.
- Data Loss Prevention: Leverage the cloud-native solution with built-in protection.
- Hybrid, SaaS Data Support: Purview protects your data no matter where it lives, whether it’s in the cloud, your own servers or an integrated partner ecosystem.
Top Four Reasons To Use Microsoft Purview
- Simplicity: Easy to get started with built-in protection, no additional agents, and an optimal user experience.
- Integration: Single portal for management and secure collaboration, built into productivity tools.
- Intelligence: Automated data security with machine learning-driven data classification and dynamic data loss prevention.
- Unification: Improve operational efficiency with a unified SIEM and XDR experience.
Microsoft Purview Is A Proven Solution
Microsoft is a recognized leader in cybersecurity, earning top positions in both Forrester Wave and New Wave reports. Its industry-leading security measures include:
- Vigilant monitoring of nation-state groups
- Thorough threat analysis
- Substantial investments in the ongoing battle against cybercrime

The impact of Microsoft Security is tangible, with organizations reporting an impressive 96% reduction in the time spent monitoring potential suspicious activities. Leveraging key tools such as Microsoft Sentinel, Microsoft 365 Defender, and Microsoft Defender for Cloud has resulted in a substantial 60% decrease in the risk of material breaches for organizations. Furthermore, reports highlight the integration of automation and process enhancements within Microsoft 365 Defender:
- Fortifies security
- Translates into an additional $10.5 million in end-user productivity
Lastly, network-related IT work experiences a remarkable 73% improvement in efficiency with the implementation of Azure Network Security. Overall, it’s clear Microsoft is committed to enhancing the overall cybersecurity posture, globally.
“The reason Microsoft provides such a powerful security solution is that it seeks to meet your needs holistically. Each security layer talks to everything else, including those data sources you might be using that are external to Microsoft.”
Kiran Ramineni
Vice President
Fannie Mae

“We needed to precisely identify which Microsoft 365 productivity applications should be classified for internal or external use. Using a container label to differentiate permissions meant users could access a single document within a team or SharePoint site and the same users could not accidentally stumble upon confidential documents, a key element of the Microsoft Purview Information Protection solution that we couldn’t get from any other solution on the market.”
Usman Abubakar Ehimeakhe
Assistant Director, Technical Lead of Microsoft 365 Services
EY
How To Improve Your Cybersecurity Today
By choosing Microsoft Purview and partnering with SPK and Associates, you can unlock the full potential of your data security strategy. The advantages extend beyond protection, encompassing ease of use, strategic insights, and significant cost savings.
Elevate your data security initiatives with SPK and Associates as your trusted Microsoft Partner.