From time to time, if you are administering a PTC Integrity Lifecycle Manager you’ll need to be able to log into PTC Integrity as one of the users you support. If you want to avoid requesting their password (if your company uses LDAP to synchronize everyone’s PTC Integrity password with their corporate password, sharing passwords with anyone is not a good idea security wise), or forcibly resetting their password in the MKS Domain (if you use that), you can use something called impersonation.
NOTE: Impersonation can be a potential security hole. There is the possibility for a user to perform actions that are logged as another user who could potentially have administrator permissions.
In order to try to avoid any potential security pitfalls, the example I am going to walk through below will demonstrate how you can configure your administrator account (and only your administrator account) to impersonate other users.
Before you can start impersonating people on your PTC Integrity Lifecycle Manager server you need to create an ACL (Access Control List) to define who has access to the permission to do this.
To set up the Impersonation ACL in PTC Integrity Lifecycle Manager, perform the following steps:
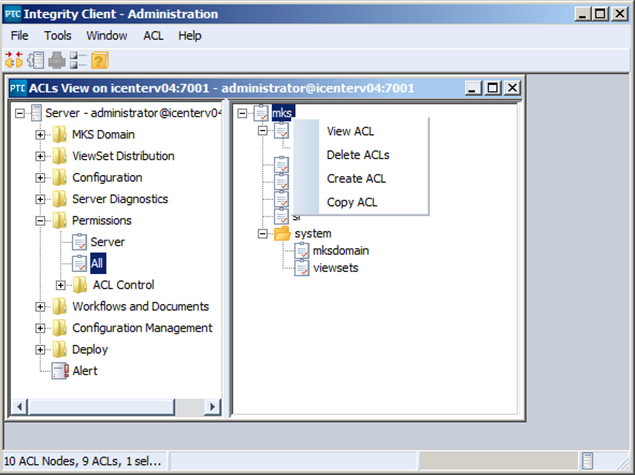
1) In the PTC Integrity Administration client, expand the Permissions section and select the “All” node.
2) Next, right click on the mks ACL group, and select “Create ACL.”
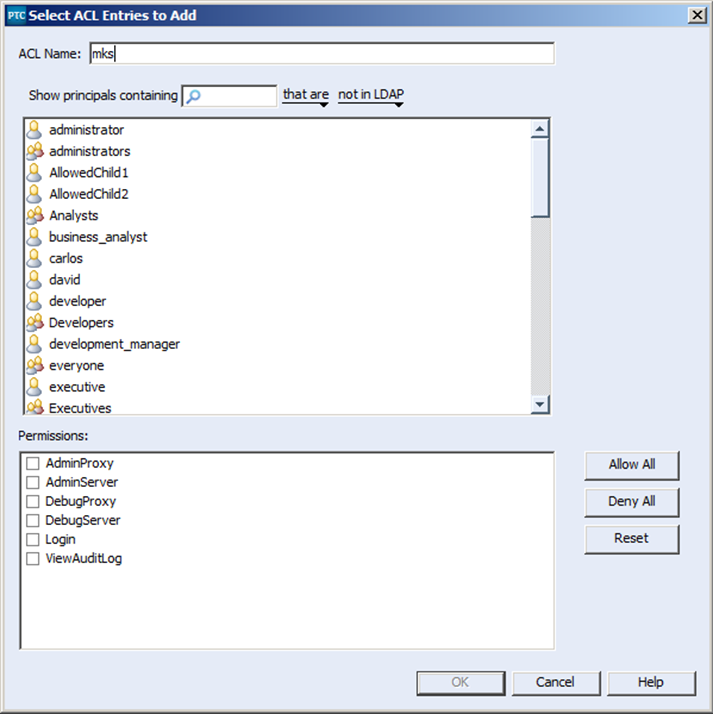
3) This will open the “Select ACL Entries to Add” dialog
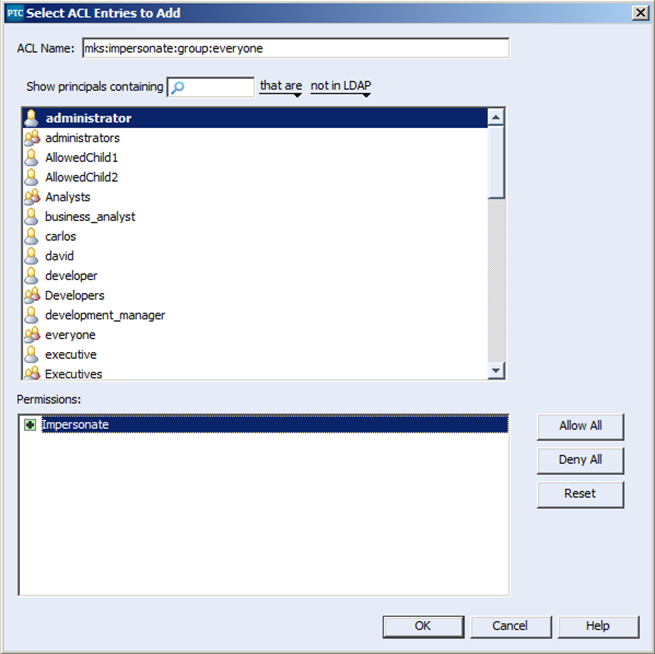
4) Next, define the user or group you wish to allow impersonation of. In this case I want to allow for the impersonation of the “everyone” group. Therefore I have named the ACL mks:impersonate:group:everyone
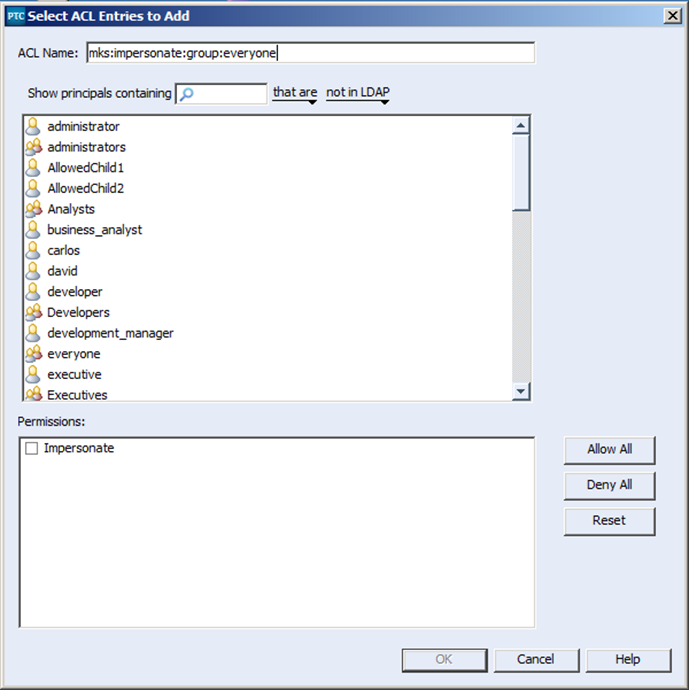
5) Last but not least, I select the administrator user, to implicitly state which user has permissions to impersonate under this ACL.
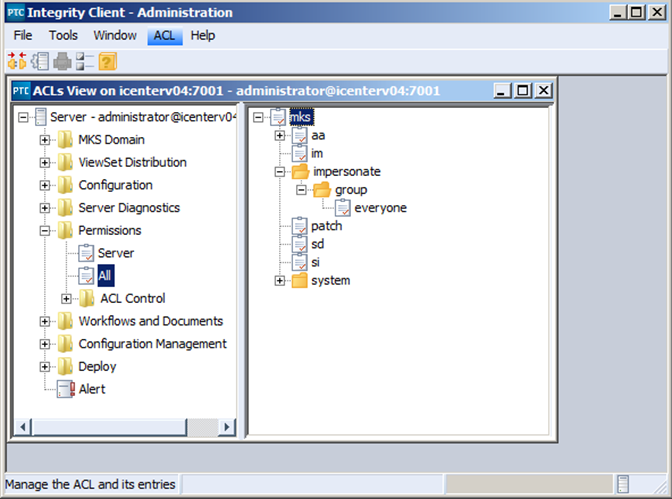
6) Once you select “OK” to apply your new ACL you will see it appear in the ACL lis
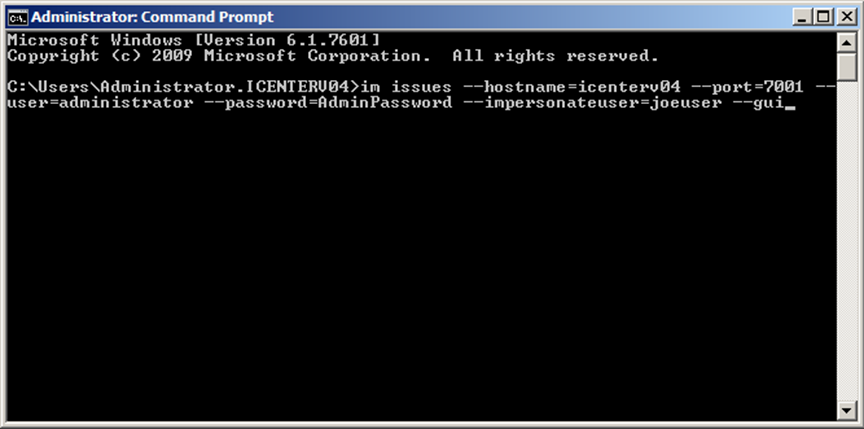
Creating the ACL to allow for impersonation is just the first step. If you actually want to perform Impersonation you need to invoke it from a command prompt window. You cannot invoke impersonation through the GUI. You can use the command line to create a GUI session and instantiate the connection using the impersonateuser flag to create a session as the impersonated user. The command to do so is as follows:
im issues –hostname=serverHost –port=serverPort –user=administrator –password=yourAdminPass –impersonateuser=impersonatedUser –gui
This in turn will open the following window for you:
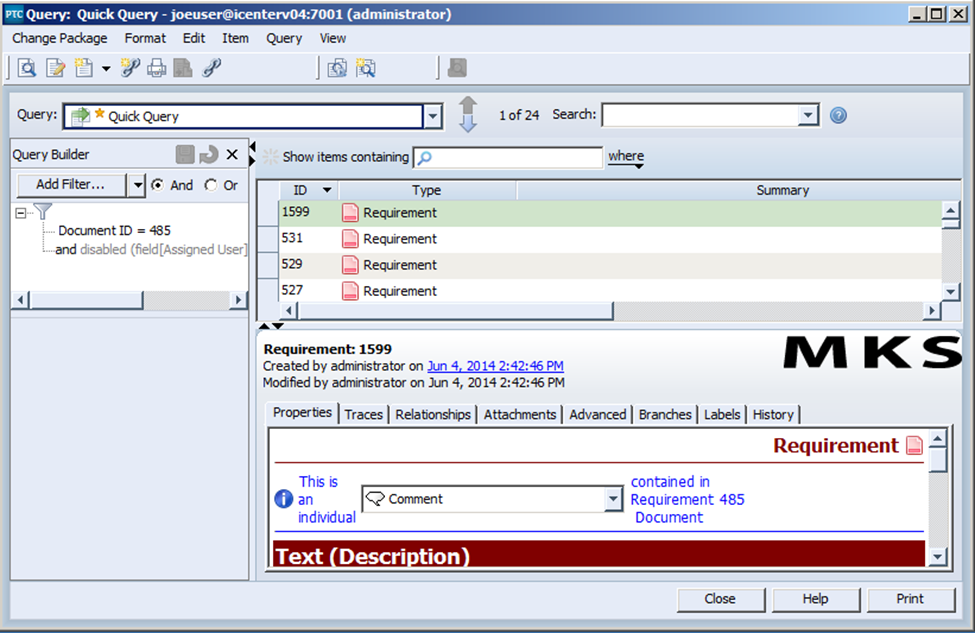
From here, everything that is performed will be as if you were logged in directly as a given user in the system. And best of all, the only people who will have access to this impersonation functionality as it is configured are those people who already have access to your administrator account.
The ability to impersonate any given person within your PTC Integrity server can go a long way in determining what the problem is when one of your users calls you complaining that a certain trigger or critical piece of functionality isn’t working.
Next Steps:
- Contact SPK and Associates to see how we can help your organization with our ALM, PLM, and Engineering Tools Support services.
- Read our White Papers & Case Studies for examples of how SPK leverages technology to advance engineering and business for our clients.