I'm a huge fan of automation, especially when it comes to installing software. With a simple one-click solution, you can setup software on a user's workstation with little or no impact on your work load. In fact, you don't even need to do the installation -- users can...
Engineering Operations
To SSD or not to SSD
What is an SSD? The term SSD (Solid State Drive), can refer to any drive that uses solid state components to store information, or more to the point - has no moving parts. When we hear terms like 'Flash Drive' or 'Thumb Drive', we typically don't think SSD, but...
A Brief History of Automated Builds
Almost every programming book starts with an example of a small program which can be compiled from the command line using a simple call to the compiler with maybe a few flags. Known as “Hello World”, the few lines of code needed to output the text is almost universal....
Upgrade to HWMonitor Pro and Make Your Computer’s Sensors Work For You!
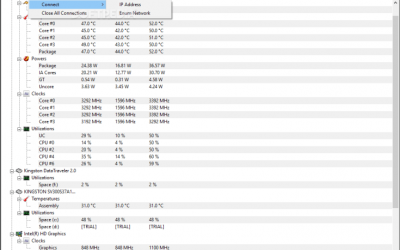
Some time ago, I wrote an article about CPUID’s wonderful tool, HWMonitor. Today I want to follow up on that and give a few tips on how to make it more useful. Firstly, HWMonitor is a free tool, but CPUID publishes a Professional version of the product, predictably...
5 Minutes with Windows 8 and Office 2013
Dell Latitude ST This is the Dell Latitude ST, which can be had from the Dell Outlet store for about $300. It’s a 10-inch tablet slate running an Atom Z670 and 2GB of RAM – like a Netbook without a keyboard. Instead, it has an N-trig digitizer that supports both...
Do you Think an Engineering Employee is Really Cheaper Than a Consultant? … Think Again.
Occasionally I’ll get a comment from a potential client who is particularly price sensitive about the rates for our consultants, and the comment usually goes something like: “I can hire a full-time employee who would cost me a lot less than what you are going to...
Avoid Budget Overruns and Unhappy Customers with Better QA and Testing
Any project can be divided into different parts including requirements gathering, design, implementation, documentation and so on. One key aspect of the project lifecycle is quality assurance (QA), but it's often overlooked. Although almost all project managers...
Using SSH to Securely Tunnel a TCP Application
Often times, I'm caught in a situation where an application or service is not directly accessible to me from the network I'm currently on. For instance, if I'm at a customer site, I may need VNC or RDP access to a collocated server. Sure, I could open up port 5901...
The Project Management Skills Gap
When it comes to product innovation and project development, the role of the project manager cannot be underestimated. That's why it's important to take an objective look at the skills and resources available in your organization and determine if a skills gap exists...
Avoid Fatal Product Design Flaws with QA
The difference between quality assurance (QA) and testing is often misunderstood. In fact, the terms are frequently used interchangeably. However, testing is actually just one part of QA. Quality assurance, on the other hand, covers a larger, more holistic part of the...
Deploying IPv6 on a Cisco IOS router with a Tunnel Broker
The time has finally come! Just a few days ago, major internet companies participated in IPv6 Launch Day – meaning from this point forward, they will be running their production systems and making their services available to you via the IPv6 in addition to IPv4....
LinkedIn Password Database Leaked!
LinkedIn, the social network for professionals, has reported that its user database has been hacked and the encrypted passwords of 6+ million users have been stolen. Even though the password database was encrypted, users with weak passwords could be exposed with...